5 Steps to Set Up AWS Incident Manager
Learn how to set up AWS Incident Manager effectively with a step-by-step guide that enhances your incident response strategy and minimizes downtime.
Need a reliable way to manage AWS incidents? AWS Incident Manager streamlines issue detection, automates responses, and keeps your team ready for anything. Here's a quick guide to get started:
- Step 1: Configure access permissions and set up roles in the Incident Manager console.
- Step 2: Create detailed response plans with clear escalation paths and alert rules.
- Step 3: Integrate monitoring tools like CloudWatch to trigger alerts and track resources.
- Step 4: Test your setup with controlled incidents to ensure everything works as planned.
- Step 5: Use insights from testing to refine response plans and improve system reliability.
Quick Tip: Start small, automate repetitive tasks, and keep your response plans updated to handle incidents effectively. Follow these steps to minimise downtime and keep your services running smoothly.
AWS Systems Manager Incident Manager - AWS Virtual ...
Before You Begin
Get your incident response framework in place before configuring AWS Incident Manager. This will help ensure a smoother setup and more effective handling of incidents.
Assemble Your Response Team
Start by pulling together your response team:
- Primary responders: Choose individuals with the expertise to diagnose and fix issues.
- Secondary support: Assign backup contacts and management-level support.
- On-call schedule: Create a schedule to ensure someone is always available.
Make sure to document everyone's contact details, preferred notification methods, and backup options for times like holidays or unexpected absences.
Understand AWS Systems Manager
Brush up on the fundamentals of AWS Systems Manager, as it plays a key role in incident management:
- SSM Agent: Check that the agent is installed on all your managed instances.
- Parameter Store: Learn how to securely store and retrieve configuration data.
- Automation Documents: Familiarise yourself with creating and using automation runbooks.
- Resource Groups: Use these to organise resources for easier incident tracking.
Once your team is ready and you’ve reviewed these basics, you can move on to setting up Incident Manager.
Step 1: Open Incident Manager
With your team ready and the basics of Systems Manager in place, it's time to access AWS Incident Manager and start the configuration process.
Locate the Incident Manager Console
You can access Incident Manager via the AWS Management Console. If you're unsure about navigation, refer to the AWS documentation for guidance.
Choose Your Region
Select a region that aligns with your operational and compliance requirements. For operations in the UK, the London region (eu-west-2) is a suitable choice. Keep these factors in mind:
- The proximity of resources and deployment locations
- Compliance with regulatory standards
- Optimising response times
Configure Access Permissions
Set up access permissions using AWS Identity and Access Management (IAM). Follow these steps:
- Create IAM roles for key participants, such as Incident Managers, Responders, and Observers.
-
Assign permissions based on the responsibilities of each role:
Permission Level Access Rights Typical Role Full Access Create or modify response plans, manage incidents Incident Managers Responder View or update incidents, execute response plans Incident Responders Observer View-only access to incidents and analytics Stakeholders - If you're managing multiple AWS accounts, set up cross-account access by establishing trust relationships and creating the necessary IAM roles.
Next, you'll move on to creating response plans for your incident management setup.
Step 2: Build Response Plans
Using the permissions established in Step 1, it's time to create detailed response plans for handling incidents. These plans should clearly outline how to address each situation effectively.
Set Incident Categories
Organise incidents based on their nature and severity to streamline responses:
| Severity Level | Impact | Response Time (max) | Example Scenario |
|---|---|---|---|
| Critical (P1) | Service outage affecting all users | 15 minutes | Database cluster failure |
| High (P2) | Significant service degradation | 30 minutes | API performance issues |
| Medium (P3) | Limited impact | 2 hours | Non-critical service errors |
| Low (P4) | Minimal disruption | 24 hours | Minor UI/UX issues |
Every category should include:
- A clear title that identifies the issue type.
- Criteria to assess the impact.
- Defined response steps.
- Escalation thresholds to ensure timely action.
Create Alert Rules
Set up alert rules to ensure swift notification of the right team members:
- Use primary methods like SMS or email for critical incidents.
- Configure secondary notification methods as backups.
- Enforce escalation if no response is received within 15 minutes.
Add Team Contacts
Keep team contact details well-organised to enable quick coordination:
- Identify primary responders who provide 24/7 coverage.
- Establish clear escalation paths with at least three levels of hierarchy.
- Automate status updates to keep stakeholders informed throughout the incident.
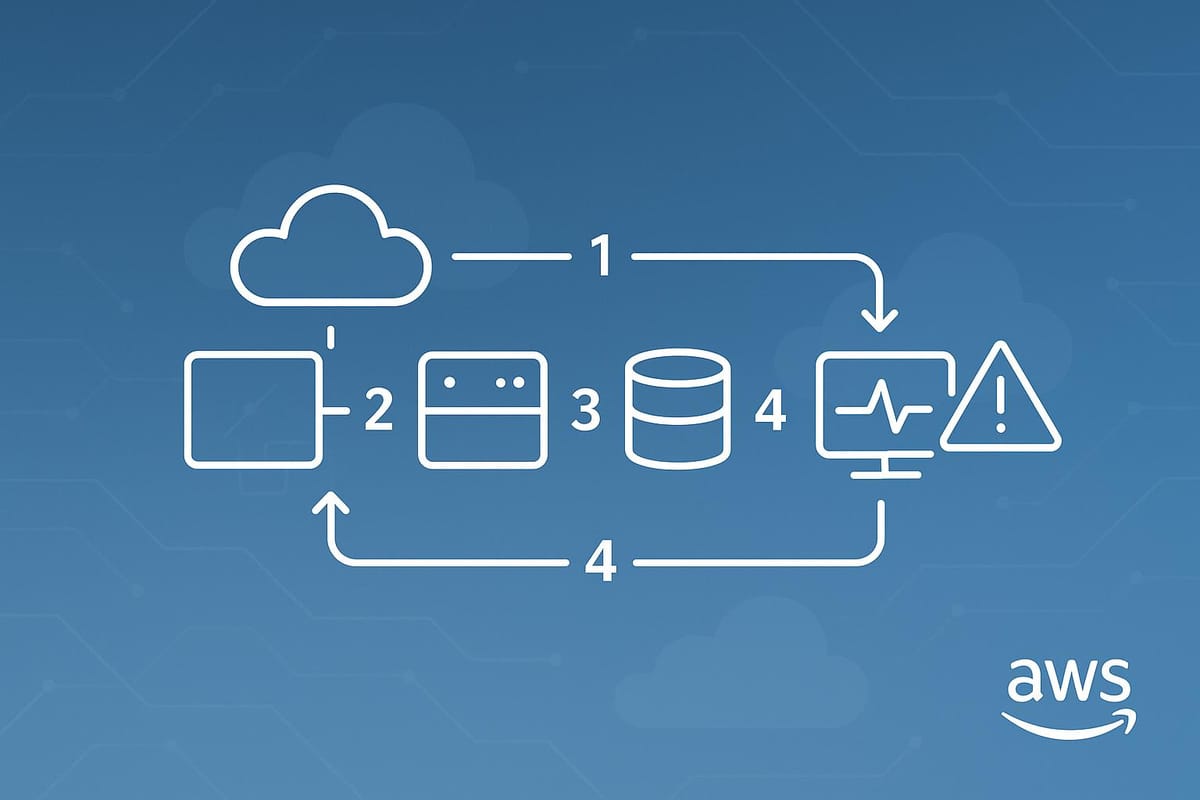
Step 3: Connect Monitoring Tools
Integrate AWS monitoring tools to quickly identify and address incidents as they arise. This setup allows you to respond to issues without delay.
Link CloudWatch Alerts
Set up CloudWatch to trigger alerts when specific metrics go beyond predefined thresholds. Keep an eye on key metrics like CPU usage, memory consumption, error rates, and API latency.
To configure alerts in the CloudWatch console:
- Select "Alarms" and create a new alarm for the metrics you want to monitor.
- Under "Actions", choose AWS Incident Manager as the target.
This setup ensures alerts are triggered immediately, helping you stay on top of incidents.
Set Up Resource Tracking
Keep track of these critical AWS services:
- EC2 Instances: Monitor CPU usage, memory, and network performance.
- RDS Databases: Check connection counts, query efficiency, and storage usage.
- S3 Buckets: Track request rates, latency, and error occurrences.
Adjust thresholds based on your application's specific requirements for better accuracy.
Create Alert Priorities
Organise incidents by their potential impact on your business. Define clear response times and notification methods for different severity levels. Use automated escalation rules to increase priority for unresolved incidents, ensuring they are addressed by the right team members. This structured system helps you manage critical issues effectively and efficiently.
Step 4: Test Your Setup
Testing your AWS Incident Manager setup helps identify gaps and strengthen your incident response process.
With monitoring tools integrated, it's time to ensure all alerts and responses work as planned.
Run Test Incidents
Conduct controlled test scenarios to evaluate your setup:
- Simple Alert Test: Trigger a CloudWatch alarm by temporarily adjusting thresholds to confirm alerts are functioning.
- Response Time Check: Assess how quickly notifications are delivered to team members.
- Escalation Path Test: Confirm that unresolved incidents escalate correctly to the next level.
Define clear success criteria for each test, such as acceptable response times and proper escalation handling. After testing, review system logs to ensure the outcomes align with expectations.
Check System Logs
Analyse logs to validate system performance:
- Alert Delivery: Ensure all team members received the notifications.
- Response Actions: Confirm that any automated responses were executed as intended.
- Integration Status: Verify that connected monitoring tools provided the expected data.
Log any anomalies in a centralised system for future improvements.
Update Your Plans
Use insights from testing and log reviews to refine your incident response strategy:
- Adjust Response Plans: Update thresholds, availability schedules, escalation timings, and communication methods based on test results.
- Incorporate Team Feedback: Collect input from participants on:
- Alert clarity
- Documentation of response procedures
- Ease of tool access
- Communication process effectiveness
- Revise Documentation: Keep your documentation up-to-date with:
- Detailed response guides
- Contact hierarchies
- System access instructions
- Common troubleshooting steps
These updates will ensure your team is better prepared for real-world incidents.
AWS Tips for Small Businesses
With Incident Manager in place, you can make it more effective by applying these practical tips. Here's how small businesses can get the most out of their AWS Incident Manager setup:
Start Small and Scale Over Time
Begin with the features that address your immediate needs. As your business grows, expand your setup by:
- Automating responses for recurring incidents.
- Adding more advanced alert rules to fine-tune notifications.
- Enhancing team response protocols to match evolving requirements.
Cut Costs with Automation
Using Infrastructure as Code (IaC) ensures consistent and error-free deployments of Incident Manager. This method:
- Minimises manual mistakes, ensuring uniform configurations.
- Makes it easier to scale as your needs change.
Best Practices for Integration
Integrating AWS managed services can improve your incident management process. Here’s how key services can help:
| Service | Purpose | How It Helps |
|---|---|---|
| CloudWatch | Monitoring and Alerts | Tracks metrics and sends alerts when thresholds are breached. |
| Systems Manager | Resource Management | Simplifies access to affected resources during incidents. |
| EventBridge | Event Routing | Automates incident creation based on system events. |
These integrations strengthen your ability to monitor and respond to incidents effectively.
Develop a Monitoring Framework
A solid monitoring strategy ensures you stay ahead of potential issues. Focus on:
- Setting alert thresholds based on historical performance data.
- Creating tiered response plans tailored to different severity levels.
- Regularly analysing incident trends to uncover recurring problems.
Keep Resources in Check
Efficient resource management helps control costs. To optimise your setup:
- Adjust alert thresholds periodically to avoid notification fatigue.
- Automate cleanup of resolved incidents to save on storage costs.
- Use targeted notifications to prevent unnecessary escalations.
For more in-depth advice on AWS cost management and scaling, check out the AWS for SMBs blog by Critical Cloud. Their expertise can guide you in creating a cost-efficient incident management system while maintaining strong operational performance.
Conclusion
Now that you've set up AWS Incident Manager step by step, it's crucial to focus on keeping it running smoothly and effectively.
A properly configured AWS Incident Manager can speed up incident resolution and minimise downtime. To keep it functioning at its best, make sure to:
- Review and update response plans regularly: Adjust them based on patterns from past incidents.
- Fine-tune alert thresholds: Avoid overwhelming your team with unnecessary alerts.
- Keep documentation clear and up to date: Ensure resolution guides are easy to follow and reflect current processes.
Incident management isn't just about reacting; it’s also about learning. Use AWS Incident Manager's analytics tools to spot trends and take proactive steps to improve your system's reliability.
To get the most out of it, integrate AWS Incident Manager with your existing tools and test its setup frequently. This ensures it remains aligned with your evolving infrastructure and meets your organisation's needs effectively.
FAQs
How do I keep my response plans effective and up-to-date after configuring AWS Incident Manager?
To ensure your response plans remain effective and up-to-date, regularly review and test them using simulated incidents. This helps identify any gaps or areas for improvement. Additionally, update your plans whenever there are changes to your organisation’s infrastructure, team structure, or workflows to ensure they stay relevant.
Engage your team by conducting periodic training sessions so everyone understands their roles and responsibilities during an incident. Keeping communication channels clear and ensuring all stakeholders are familiar with the process will further enhance the effectiveness of your response plans.
How can I integrate AWS Incident Manager with monitoring tools like CloudWatch?
To integrate AWS Incident Manager with monitoring tools like CloudWatch, ensure you configure CloudWatch alarms to trigger incidents in AWS Incident Manager. Start by linking your CloudWatch metrics to alarms that align with your organisation's incident response needs. Then, connect these alarms to response plans in Incident Manager, which can automate actions such as notifying responders or running mitigation workflows.
This integration streamlines incident detection and resolution, helping small and medium-sized businesses enhance their operational efficiency. For further guidance on optimising AWS services for SMBs, consider exploring expert resources tailored to cost and performance best practices.
How does selecting an AWS region affect the performance and compliance of AWS Incident Manager?
Choosing the right AWS region is crucial for optimising the performance and compliance of AWS Incident Manager. Regions closer to your users can reduce latency, ensuring faster response times during critical incidents. Additionally, selecting a region that aligns with local data residency and compliance requirements helps meet legal and regulatory standards, especially for SMBs operating in the UK or the EU.
When configuring AWS Incident Manager, consider factors like proximity to your primary user base, data sovereignty laws, and service availability in the region to ensure both efficiency and compliance.